 This is a covert operative’s guide to air-gapped systems – what they are, how they work, where they fail, how to attack them, and how you can implement air-gapped security principles in your own environment.
This is a covert operative’s guide to air-gapped systems – what they are, how they work, where they fail, how to attack them, and how you can implement air-gapped security principles in your own environment.
![]()
The most absolute assurance in digital security requires disconnecting absolutely.
Air-gapped systems are among the most secure forms of digital infrastructure in existence. When properly implemented and maintained, they can act as the last line of defense against advanced persistent threats (APTs), hostile foreign actors, and insider sabotage. In covert operations and national security, air-gapped systems are often used to store and process the most sensitive intelligence, materials that would be catastrophic to compromise.
Connectivity invites attack. Isolation denies it.
This principle isn’t just for classified intelligence or clandestine work; it has practical, everyday “normal” applications as well. A journalist protecting their sources, a privacy-conscious civilian storing cryptocurrency keys, or a vigilant individual who wants to reduce digital exposure, air-gapped security offers a powerful layer of protection against cyber threats.
![]()
![]()
![]()
![]()
WHAT IS AN AIR-GAPPED SYSTEM?
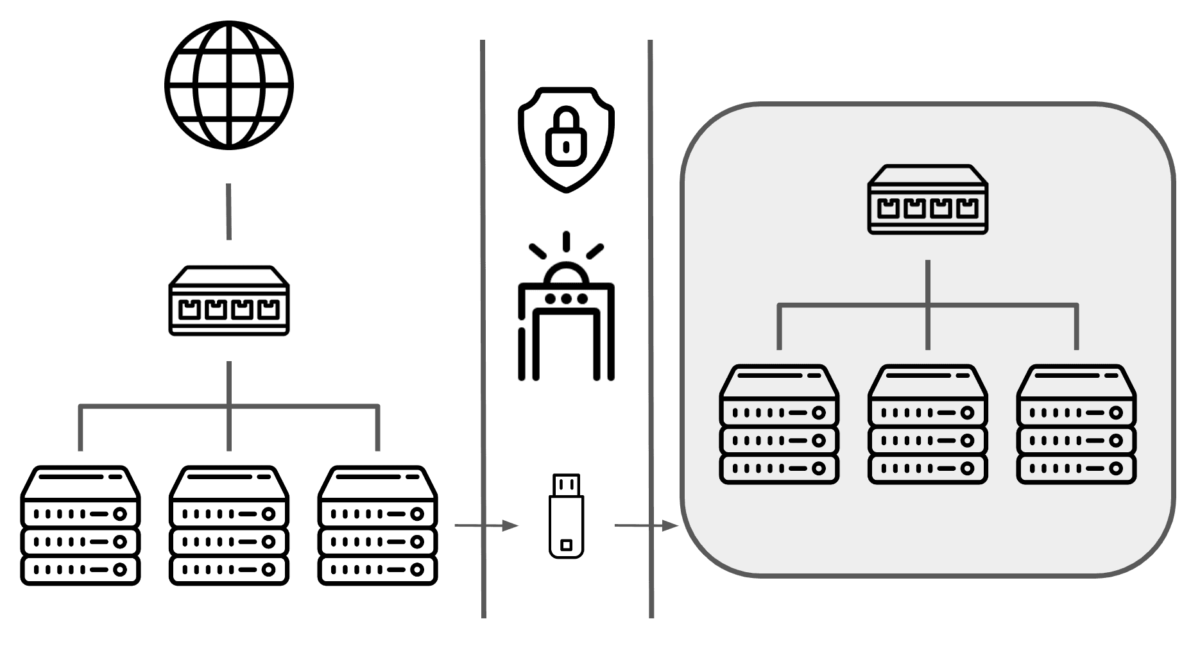
An air-gapped system is a computer, device or network that’s physically isolated from unsecured networks like the public internet or even a local intranet. It has no network interfaces (wired or wireless) that connect to other systems. In short, you can’t access it remotely, and it can’t “talk” to the outside world unless you physically move data in or out.
This concept isn’t new. Before the internet, this was the default state of most sensitive computing environments. Today, it’s used selectively when the stakes are too high to allow any sort of digital exposure.
Nuclear Command and Control Systems
These systems are separated from all external networks to prevent unauthorized access or remote detonation risks.
Home Setups for Digital Privacy Advocates
Using an offline laptop for journaling, personal files, or private financial records can greatly reduce surveillance exposure.
Cryptographic Key Management for Top-Secret Data
Air-gapped systems store and generate cryptographic material that, if compromised, would render entire security structures vulnerable.
Air-gapped Cold Wallets for Cryptocurrency
Private keys for Bitcoin or Monero is stored offline to prevent theft from malware or remote hackers.
Military Targeting and Weapons Guidance Systems
To prevent remote manipulation or spoofing, weapon control systems often operate in isolated environments.
Sensitive Research Environments (e.g., black projects or advanced AI systems)
Prevents both espionage and uncontrolled dissemination of dangerous or proprietary technologies.
Storage of CIA NOC Personnel Files or Field Asset Identities
The identities of operatives working under non-official cover are among the most protected secrets in the intelligence community.
Industrial Control Systems (ICS) and SCADA Networks
Facilities like power plants and water treatment centers often isolate critical control systems to protect against cyber intrusion.
Offline Backup Servers for Law Firms, Clinics, or Financial Institutions
Isolated archives can prevent ransomware from encrypting all available data during a network breach.
Research Labs Handling Pandemic-Level Biohazards
Systems that log experiment data are often air-gapped to prevent potential bio-cyber terrorism or unauthorized access.
⸻
It’s a barrier, a hard stop that separates your most valuable or dangerous information from the digital battlefield. It enforces a slower, more deliberate flow of data, which is both a strength and a challenge. But in environments where compromise equals catastrophe, that friction is essential.
![]()
![]()
BENEFITS OF AIR-GAPPED SECURITY
Reduced Attack Surface
With no internet access or external connectivity, typical cyber attacks; malware, phishing, remote access trojans, become nearly impossible unless the attacker has physical access.
High Containment
Even if a system is compromised, the damage is contained. There’s no easy lateral movement to other networks.
Operational Discipline
Access control and data movement are deliberate, often requiring two-person protocols or logging procedures. This enforces a mindset of caution and accountability.
Resilience to Supply Chain Attacks
While not immune, air-gapped systems can be designed and built in-house using known hardware and software with zero outside dependencies, limiting risk exposure.
Long-Term Data Preservation
Isolated systems are ideal for storing critical records, archival material, or forensic logs without fear of silent corruption, deletion, or unauthorized alteration over time.
Immunity to Remote Surveillance
Air-gapped systems can’t be monitored or accessed remotely, making them immune to spyware, mass surveillance programs, or foreign intelligence collection via digital backdoors.
![]()
![]()

![]()
![]()
RISKS AND ATTACK VECTORS
Air-gapped systems are not invincible. Intelligence services have developed and demonstrated ways to bridge these “air gaps” using a mix of physical access, electromagnetic emissions, and human manipulation.
Removable Media (USB Drives)
The most common breach vector. An operative unknowingly uses a compromised USB device to transfer data, and malware executes on the air-gapped machine. Example: Stuxnet (2009), which targeted Iranian centrifuge systems.
Electromagnetic Emissions
Covert operatives or SIGINT teams can exploit unintended radio-frequency emissions from monitors, keyboards, or power cables. Using specialized antennas, they can reconstruct what’s being typed or displayed (example: TEMPEST attacks).
Acoustic Signaling
Data can be exfiltrated via audio, inaudible frequencies transmitted through speakers and picked up by nearby microphones. Not fast, but enough to leak encryption keys or logs.
Thermal or Optical Exfiltration
In extreme cases, malware can use fan speed or drive activity LEDs to send out binary signals. Surveillance equipment like hidden cameras can capture and decode this.
Compromised Supply Chain
Preloaded firmware or implants at the BIOS or chipset level can allow a system to “phone home” when eventually connected, or leak via side channels even before that.
⸻
The reality is that air-gapped systems shift the threat from digital to physical, requiring the attacker to be far more creative and resourceful. That doesn’t mean the system is weak, only that your tradecraft and physical security must rise to meet the threat.
![]()
![]()
TRADECRAFT GUIDELINE
Setting up an air-gapped system is only the beginning. The real security comes from how it’s maintained over time, through strict access controls, disciplined operational behavior, and a hard separation between trusted and untrusted environments.
Physical Isolation
Controlled Removable Media Workflow
Personnel Training and Insider Threat Controls
Hardened Software Environment
No Cross-Pollination
⸻
Even the most secure hardware is only as trustworthy as the discipline of those who use it. Treat every interaction with an air-gapped system as a deliberate, logged event, not casual computing. The key to long-term operational security isn’t just building a strong perimeter, it’s protecting it with unwavering habits.
![]()
![]()

![]()
![]()
CIVILIAN AND OPERATIONAL
Even outside classified environments, the air-gap model has real utility. If you’re handling whistleblower data, organizing covert meetings, or storing information that could jeopardize lives if leaked, air-gapping offers a trustworthy fallback.
• Keep a non-networked laptop for sensitive notes, drafts, and surveillance logs. This ensures intelligence or personal data remains isolated from cloud syncs, malware, or metadata leaks.
• Store encryption keys offline, on physically secure media. This prevents key exposure from device compromise or credential-stealing malware.
• Use one-way data transfer principles to retrieve intelligence from sources and format them for dissemination without risking metadata leaks. Control the flow of information into and out of a secure system without exposing source material to digital threats.
• Maintain an air-gapped media archive for sensitive footage, audio, or photos. Especially useful for field operatives, journalists, or security teams capturing incriminating or classified material that cannot be leaked under any circumstance.
• Secure financial operations or high-risk transactions. Cold wallets, air-gapped accounting systems, or offline deal documentation protect against fraud, theft, or unauthorized digital surveillance.
• Create an offline emergency reference system. For disaster preparedness, air-gapped devices can store manuals, maps, medical references, or communications procedures in case of cyberattack or infrastructure collapse.
⸻
You don’t need a government clearance to apply the logic of air-gapping, just a clear understanding of what you can’t afford to lose. Where everything is now online, the offline system becomes your sanctuary.
![]()
![]()
Air-gapped systems are not about convenience, they’re about control, containment, and trust in environments where compromise is not an option. It’s a shield, not a fortress, and it’s only as strong as the person tasked with maintaining it.
![]()
// Disconnection is beyond encryption. An air gap renders your data unreachable by default.
[INTEL : Baiting a Target Into a False Sense of Control]
[OPTICS : Moscow, Russia]
![[RDCTD]](https://rdctd.pro/wp-content/uploads/RDCTD-Covert-Operative-Tradecraft-Guide-LOGO-tk.png)
![[RDCTD]](https://rdctd.pro/wp-content/uploads/RDCTD-Covert-Operative-Tradecraft-Guide-LOGO-mobile.png)

